Protect Your Applications with a Strong Password
At Ultra.cc, the security of our users is our top most priority, and we take every precaution to make sure your data is protected. However, the level of our security does not matter if your applications are without secure authentication. In this guide, we will show you how to properly create a strong password, and better protect your applications.
Use a password manager -Bitwardenis an open source password manager that can be self-hosted.Use encrypted SSH keys - Connect to your Ultra.cc service with anencrypted SSH key.
How to Create a Strong Password
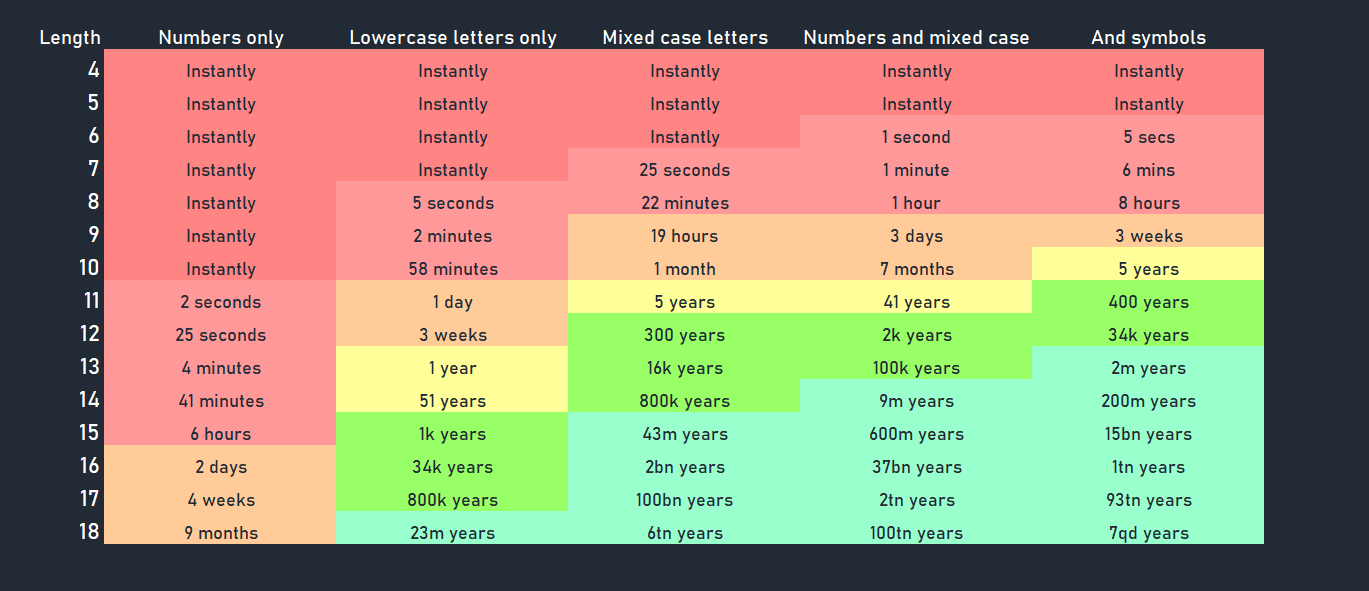
One of the most important aspects of creating a strong password is the length of the password. Even though complexity is needed to a certain degree, the length is the deciding factor of how strong a password is. As you can see from the above image, the time it will take to brute-force crack a password exponentially grows as the length increases.
Below you will find some guidelines for how to create a strong password:
- A password should be 12 characters or more; length is always better than complexity.
- A password should include a combination of
letters,letters (capital and lower-case), numbers, and characters. - A password should never be re-used or shared with other applications.
- A password should not include personal information like username or anything else that can be easily discovered.
- A password should not include basic dictionary words, such as "house".
- A password should not contain any consecutive letters or numbers.
- A password should not be the word “password” or the same letter or number repeated.
- A password should never be slightly changed for continued use.
By following the above guidelines, you will be able to create a strong password and properly secure your applications.
General OPSEC
Besides creating strong passwords to protect your applications. We would advise adopting a wider security thinking across all your domains and platforms. This is called OPSEC (operations security), and below you can find the 5 steps of OPSEC.
- Identify critical information
- Analyze threats
- Analyze vulnerabilities
- Assess risks
- Apply appropriate countermeasures
In short, OPSEC can be described as; what are the threats, and how do I best protect myself? As this is a very large subject, we will not go into further details. However, we urge everyone to adopt OPSEC into their digital life, if not only to a certain degree.
Below you will find some general recommendations on how you can further secure your presence online.
- Use a password manager - Bitwarden is an open source password manager that can be self-hosted.
- Use encrypted SSH keys - Connect to your Ultra.cc service with an encrypted SSH key.
- Adopt the Diceware passphrase method - Create memorable passphrases instead of hard to remember passwords.
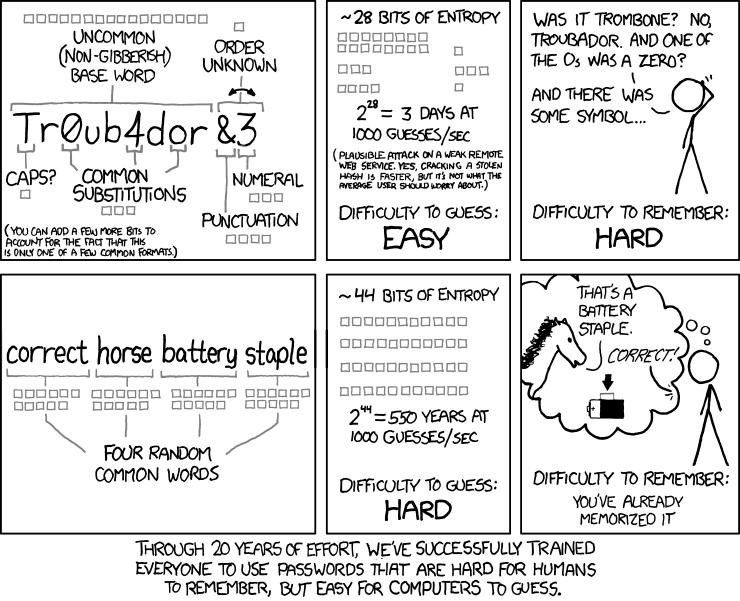
The above image is a creation of xkcd.com